Open Source Your Knowledge, Become a Contributor
Technology knowledge has to be shared and made accessible for free. Join the movement.

Starting
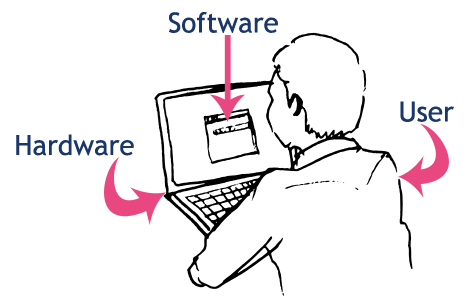
To understand computer & hacking, it's necessary to see that a computer system is composed by 3 main components : hardware, software and human. Hardware is the physical part of the system. Software is the logical part of the system. And human is the creator, and the user.
Each part is important when we talk about hacking : they all have their vulnerabilities. Some examples :
- IPhone Jailbreak : Hardware
- SQL Injection : Software
- Social Engineering : Human
An illustration with Hackmyfortress.com :
- Hardware : servers where are the site and the database
- Software : the webserver
- Human : creators/administrators of the website
To understand how works IT, know the history of computing technologies is primordial.
History of computer
The birth of computers comes from Turing and the famous Turing Machine. The concept of this machine is purely abstract: a reading head reads an infinite ribbon. This ribbon is composed of boxes in which there are symbols coming from a known alphabet. Reading this ribbon allows you to perform actions, such as replacing the symbol in the current cell, and reading another box on the ribbon. By creating an alphabet composed of 0 and 1, we arrive at the binary model, the current model of computer.
An example of interactive Turing Machine
The beginning of computer
Mainframe
The first real computer was the big ENIAC (Electrical Numerical Integrator and Calculator) machine, created by John W. Mauchly and J. Presper Eckert at the University of Pennsylvania. It used words of ten decimal digits instead of binary. ENIAC machine used more than 15 000 vacuum tube (also named thermionic valve, or lamp). ENIAC was Turing-complete : it can be programmed to resolve all problems. Vacuum tubes are fragiles and are very hot when ENIAC works, so, when an insect burned on a lamp, the lamp explode. They call it : a bug. The executable instructions of ENIAC programs were stored in separate units, which were plugged to form a route.
Curious ?

Around the 1950s appeared the transistor : more efficient and smaller, it has replaced big lamp and is present in radios, computers, amplifier ...
In the 1960s, thanks to the transistor, IBM has developped mainframes and was the leader in computer. But mainframes was exepensive, large, and difficult to use.
Personal computer, or PC
In the 1970s, thanks to Steve Jobs and Steve Wozniak, with their Apple II, the PC was born. It could be programmed with BASIC language, and programs could be stored on audio-cassette recorder.
In 1984 appeared the Graphical User Interface (GUI) and the mouse. Also in 1984, Richard Stallman launched is project GNU. In 1985, Windows 1.01 is officialy released.
In 1991, Linux Torvald started is project of Linux Kernel. Today, most of web servers work with a GNU/Linux system.
History of hacking
'Hacker' or 'Hacking' come from the 1960s when students of MIT founded the TMRC (Tech Model Railroad Club). The WECo (Western Electric Co.) give them some telephones and cross-bars. Members of TMRC hacked those phones to make the first automatic system of a model railroad.
The 'Father' of hackers
In 1969, John Draper realized that the gift whistles of Cap'n Crunch cereals give a tone of 2600 hertz, the same as the AT & T telephone network to activate the long distance lines. Nicknamed Captain Crunch, he whistles in the cabin phones to make free calls anywhere in the world. He will call this technique the 'phreaking', contraction of phone and freak.
The exploits of Captain Crunch will inspire new computer hackers gathered within the: Homebrew Computer Club. Its members will modify and evolve one of the first individual computers: the Alter 8800. Among them: Steve Wozniak and Steve Jobs.
The 1980s
The world discovers hackers in 1983. Kevin Poulsen, 17, intrudes into ARPANet, the Internet's precursor network for the military. In the same year, John Badham's science fiction film 'Wargames' was released. This feature tells the story of a hacker who hijacks the US military computer system and risks triggering a global thermonuclear war. Media and the general public are discovering the 'fantasy' universe of hackers.
In 1988 the worm Morris spreads on ARPAnet and infects more than 6000 computers. Its author, Robert Tappan Morris, is sentenced to three years of judicial follow-up and a fine of $ 10,000.
1990s
With the internet, cybercrime is born and hackers are divided. On the one hand the 'black hat', often criminal activities and on the other the 'white hat' with no intention to harm and committed to making public security flaws.
Two major arrests in the 1990s. In 1994: Russian mathematician Vladimir Levin subtracts $ 10 million from Citybank, penetrating into the international banking network SWIFT. He was sentenced to three years in prison. In 1995, Kevin Mitnick was arrested by the FBI. On the run since 1989, he is accused of stealing software and intruding into protected systems. The damage is estimated at more than $ 80 million. He was sentenced to 5 years' imprisonment. When he was released, he was forbidden to access telephones, networks and computers.
2000s
The 2000s continue to be marked by cybercrime. However, hackers can blow up industrial locks, such as DVDs or smartphones. The development of politicized groups that use hacker techniques for their militant actions is another trend of the 2000s. This is the case of the highly controversial WikiLeaks, a site that leaks information while ensuring confidentiality sources. One of its founders is none other than Julian Assange, formerly known as 'Mendax', hacker of the group 'International Subversives'.